Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*Rogue anti-spyware (or rogue security software) is an application that uses malware or malicious tools to advertise or install itself or to force computer users to pay for removal of nonexistent infections. Rogue anti-spyware will often install a Trojan horse to download a trial version of the rogue anti-spyware program or it will execute other unwanted actions.
The main goal of rogue anti-spyware developers is to install and sell their product. In order to attempt to install their program, fake Windows dialog boxes and other browser pop-ups are often displayed attempting to entice the user to click on them. Usually they will display a message warning users that their computer system is infected with numerous parasites and urging the user to purchase and install the offered rogue anti-spyware application.
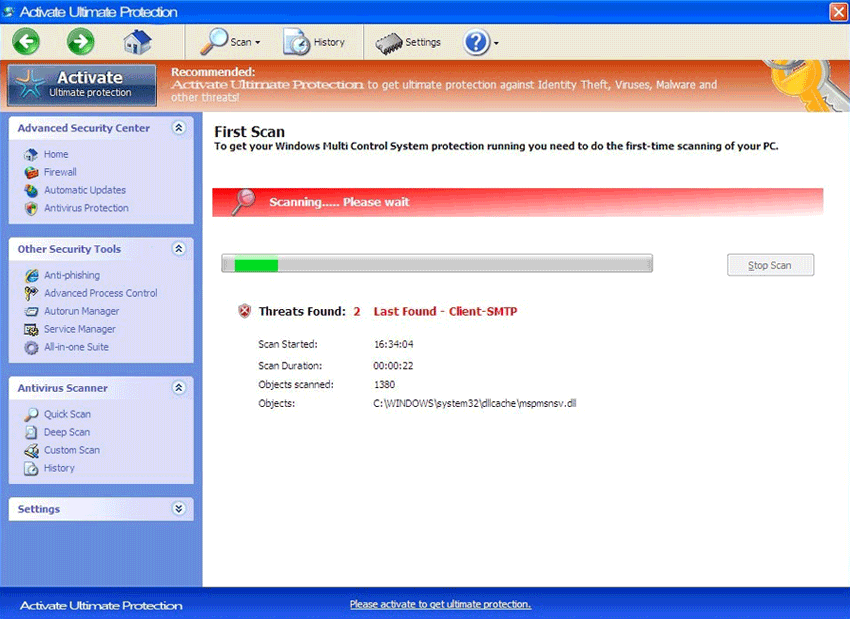
Example of a Rogue Anti-Spyware program interface
You simply must be careful when selecting an antispyware program, since there are just as many fake ones on the web as there are legitimate ones. Fake antispyware (Rogue Anti-Spyware) programs are modeled off of legitimate programs in hopes of duping wary PC users into buying empty software. A cybercriminal is ultimately behind these fake tools, although it is a Trojan engineering the presentation. Rogue Anti-Spyware programs are also similar to Rogue Anti-Virus applications, which are fake anti-virus apps that cater more to the alleged detection and removal of computer viruses.
Fake antispyware program (Rogue Anti-Spyware) presentations run the same course as most rogue security programs, too engineered by Trojans. First is the distribution vector. Trojans are great at guising their download as something innocent or helpful, so it is highly likely you or someone using your computer blindly clicked on a booby-trapped link or landed on a compromised webpage. While the booby-trapped link is dependent on the victim taking obvious action, the compromised webpage, on the other hand, can react to just a landing. If your browser is vulnerable, i.e. in need of a patch, and your system is absent stealth antimalware protection, the landing could trigger an automatic download of malware on your system. So be careful where you land and what you click on.
If the Trojan representing the fake antispyware program slips inside your computer, you can expect the following to unfold:
Fake antispyware programs are exactly that – FAKE. They cannot make good on any promises, meaning they cannot remove infections. In fact, they are the infection. Fake antispyware are the work of the devil, aka a cybercriminal, and were not designed to help you but rather cause harm.
Backdoors mimic remote assistance tools and afford a hacker remote access and control of an infected system. Often backdoors are secretly downloaded and installed on infected computers and then sold on the black market to the highest bidder. If a hacker gains remote control, he could secretly use and drain the system resources in a DNS strike and the trails of this illegal activity can lead right to your IP address and ultimately your home.
Legitimate antispyware tools are meant to filter out programs that spy on your surfing habits and make possible an assault of custom and unwanted advertisements based off key words. If a malicious BHO (browser helper object or plugin) is onboard, your web traffic could be hijacked and you could be forcibly routed to:
Unfortunately, a lot of legitimate programs as well as malicious ones are secretly collecting data and sometimes it is can be invasive. Antispyware and antimalware solutions monitor behaviors, i.e. programming and processes, and red flag ones that violate the PC’s privacy. Removing invasive programs are not always easy, especially rogue programs and this includes fake antispyware programs. Rogues often contain a rootkit, a malicious tool used to mask and bury malicious files, thus making it hard for novice PC users or subpar antimalware tools to remove them. For example, Trojans of rogue programs are quite stealth and can edit the registry so the malicious executable runs each time Windows is booted. They hide their files by labeling them the same as legitimate operating system files and too house them in the white listed area of such critical files. Many antivirus programs are not able to scan the white listed area, which means they cannot successfully combat rootkits and the malicious files they bury. Therefore, it is highly recommended you seek a formidable opponent – a stealth and professional antimalware solution equipped with an ANTIROOTKIT component to safely and successfully remove hidden malware and fully restore your system back to its normal use.
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | OpenCloud Antivirus | 100 % (High) | 4 | |
| 2. | Tarmac | |||
| 3. | Green Antivirus 2009 | 100 % (High) |
Reser.Reputation.1 Encrypted Archive Trojan.Win32.Malware.4 |
232 |
| 4. | Contravirus | 100 % (High) | 59 | |
| 5. | Cleanator | 100 % (High) | 16 | |
| 6. | SystemWarrior | 100 % (High) | 7 | |
| 7. | NoMalware | 100 % (High) |
NoMalware Win32/Adware.NoMalware TrojWare.Win32.NoMalware.~A |
8 |
| 8. | Antispyware Pro 2012 | 20 % (Normal) | ||
| 9. | SignalBalance | |||
| 10. | Weknow.ac | |||
| 11. | SystemExtr | |||
| 12. | Windows XP Fix | 100 % (High) | 11 | |
| 13. | Windows Antivirus 2008 | 100 % (High) |
TROJ_FAKEAV.KAD High Risk Cloaked Malware Win32/Adware.Antivirus2008 |
12 |
| 14. | ByteDefender | 100 % (High) | ||
| 15. | Windows 7 Fix | |||
| 16. | LightSpy | |||
| 17. | SearchArchive | |||
| 18. | WebQuestSearch | |||
| 19. | Antivirus System Pro | 100 % (High) |
Troj/FakeAV-AMU Trojan.FakeSpypro.A.38 potentially unwanted program Artemis!B3D95C587409 |
23 |
| 20. | Antivirus 2009 | 100 % (High) |
Generic11.BKKP Trojan.Win32.FraudPack.hug Trojan.FraudPack.hug |
36 |
| 21. | Smart Data Recovery | 20 % (Normal) | 299,326 | |
| 22. | Windows Secure Surfer | 20 % (Normal) |
Trojan.Win32.FakeAV Dropper/Win32.Romeo Trojan-Dropper.Win32.Dapato.awui |
260 |
| 23. | HistoryKill | 60 % (Medium) |
Heuristic.LooksLike.Trojan.Spy.Delf.C PossibleThreat Suspicious:W32/Riskware!Online |
855 |
| 24. | Privacy Protection | 100 % (High) | ||
| 25. | Total Security 2009 | 100 % (High) | 4 | |
| 26. | Security Tool | 100 % (High) |
TROJ_FAKEAV.TAM SecurityToolFraud a variant of Win32/Kryptik.DNY |
|
| 27. | Spyware Guard 2008 | 100 % (High) |
TROJ_PAKES.TA Artemis!5BD01E929CCC Trojan.Win32.Pakes.mdl |
37 |
| 28. | Activate Ultimate Protection | 20 % (Normal) | ||
| 29. | ColoredLambert | |||
| 30. | Avira Enhanced Protection Mode |
Last updated: 2024-05-16